
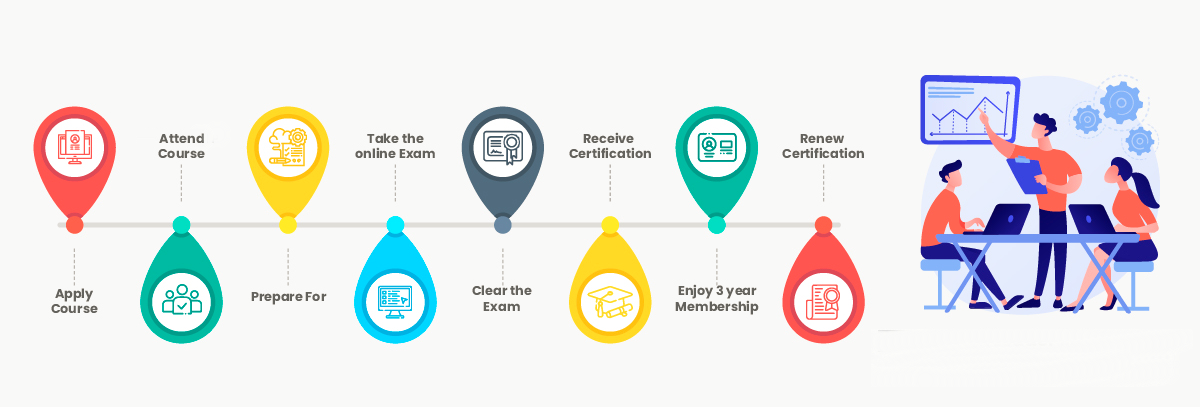
Sambodhi and Education Nest offer a Certified Ethical Hacker (CEH) training course designed to equip you with the necessary skills to become a proficient hacker and fortify your network systems against cyber-attacks. Aligned with the latest CEH v12 by the EC-Council, this hands-on training program prepares you to enhance your blue team skills. The CEH certification course focuses on essential cybersecurity skills for security and network analysts. It validates your expertise in areas like network security, session hijacking, cryptography, system penetration testing, building firewalls, footprinting, and more, making you a Certified Ethical Hacker (CEH). The training enables you to handle cybersecurity challenges and provides a comprehensive understanding of security aspects. On successful completion of the course, you will receive a Course Completion Certificate from Sambodhi and Education Nest.
Application Deadline: Jun 30, 2023
Upskill for Your Dream Job
Sambodhi and Education Nest offers a comprehensive Certified Ethical Hacker (CEH) Training Course. With live project-based training, aspiring candidates can learn from industry experts with over 10 years of experience in the field. Our instructors have developed unique teaching styles to ensure mastery of the skills and knowledge required to become a certified ethical hacker. The course covers essential topics such as network security, vulnerability assessment, penetration testing, and ethical hacking techniques. Through practical hands-on exercises and real-world scenarios, participants gain a deep understanding of hacking methodologies, tools, and countermeasures. Upon completion of the course, students are well-equipped to identify vulnerabilities, assess risks, and protect systems and networks from cyber threats.



Instructor-led Certified Ethical Hacker (CEH) live online Training Schedule
May 15th – Weekend
July 1st – Weekend
Why enroll for Certified Ethical Hacker (CEH) Certificate Training Course?
The global Certified Ethical Hacker (CEH) market is projected to grow at a CAGR of 11.2% from 2021 to 2026. The cybersecurity market is also expected to grow at a CAGR of 13.4% in 2022 to 2029.

CEH certification is globally recognized and in-demand in industries like finance, healthcare, retail, and more. As companies rely on data-driven insights, the demand for CEH professionals is projected to grow.

According to Payscale, the average salary for a Certified Ethical Hacker (CEH) professional in India ranges from INR 259k to INR 1.5m per year, depending on experience and job role.
Certified Ethical Hacker (CEH) Training Course Benefits
Sambodhi and Education Nest’s Certified Ethical Hacker (CEH) course is a valuable program for businesses seeking to enhance their cybersecurity practices. This ethical hacking certification verifies the skills necessary to succeed in the information security field and is mandatory for security-related positions in many IT departments. CEH certified professionals earn 44% more than non-certified counterparts, and being CEH certified is a badge of trust. NASSCOM reported that India alone would need 1 million cyber security professionals by 2020, while job portal Indeed reported a spike of 150 percent in cyber security roles between January 2017 and March 2018. By completing the CEH course, businesses can develop a strong understanding of security aspects and have the expertise to address cybersecurity issues.

Annual Salary

Hiring Companies
Want to become a Professional Ethical Hacker?
Why Certified Ethical Hacker (CEH) Certificate Training Course from Education Nest






Certified Ethical Hacker (CEH) Skills Covered
Certified Ethical Hacker (CEH) Training Course Syllabus
Certified Ethical Hacker (CEH) Training Projects

In the retail industry, Certified Ethical Hackers (CEH) play a crucial role in ensuring the security of sensitive customer data and protecting against cyber threats. They are responsible for conducting vulnerability assessments, identifying weaknesses in the network infrastructure, and implementing security measures to prevent data breaches and unauthorized access. CEH professionals in the retail sector work on projects such as strengthening payment systems, securing e-commerce platforms, and safeguarding customer databases. Their expertise in ethical hacking techniques, penetration testing, and risk assessment helps retailers maintain the integrity of their systems, build customer trust, and meet regulatory compliance standards. With the ever-increasing reliance on digital platforms in the retail industry, the demand for CEH professionals continues to grow to mitigate potential security risks and protect valuable consumer information.

Certified Ethical Hackers (CEH) play a crucial role in the IT industry by ensuring the security and integrity of computer systems and networks. They are responsible for identifying vulnerabilities in an organization's infrastructure and simulating real-world cyberattacks to test and strengthen their security measures. CEH professionals are in high demand across various industries, including finance, healthcare, government, and technology, where data privacy and protection are paramount. Their expertise is sought after to protect sensitive information, prevent cyber threats, and ensure compliance with industry regulations. With the increasing prevalence of cyberattacks, the need for skilled CEH professionals continues to grow, making it a lucrative and promising field in the IT industry.
Certified Ethical Hacker (CEH) Training Description
The Certified Ethical Hacker (CEH) course provides comprehensive training in ethical hacking techniques and methodologies. It equips individuals with the skills and knowledge to identify and exploit vulnerabilities in computer systems and networks, with the ultimate goal of enhancing overall security. Participants learn about various hacking tools, attack vectors, and countermeasures to protect organizations from malicious cyber threats. The course covers topics such as network scanning, system hacking, social engineering, cryptography, and web application security. Through a combination of theoretical knowledge and practical hands-on exercises, aspiring professionals gain the necessary expertise to become ethical hackers and contribute to the robustness of cybersecurity frameworks.
The objectives of the Certified Ethical Hacker (CEH) course are as follows:
There are several reasons why learning the Certified Ethical Hacker (CEH) course can be beneficial. Here are the key points:
Enhance cybersecurity skills: The CEH course equips you with in-depth knowledge and practical skills to identify vulnerabilities and strengthen the security of computer systems and networks.
Stay ahead of cyber threats: As the frequency and sophistication of cyberattacks continue to rise, organizations need professionals who can proactively identify and mitigate potential risks. CEH certification demonstrates your expertise in ethical hacking and makes you valuable in the job market.
Career opportunities: The demand for cybersecurity professionals, including ethical hackers, is growing rapidly. By gaining CEH certification, you open doors to a wide range of job opportunities in industries such as IT, finance, healthcare, government, and more.
Protect organizations from malicious hackers: With CEH skills, you can help organizations protect their sensitive data, prevent security breaches, and minimize the potential damage caused by cybercriminals.
Gain an understanding of hacker techniques: Learning ethical hacking provides insights into the mindset and techniques used by malicious hackers. This knowledge can be valuable in developing effective security measures and strategies.
Ethical hacking as a profession: Ethical hackers are hired by organizations to conduct security assessments, vulnerability testing, and penetration testing. The CEH course equips you with the necessary skills to pursue a career as an ethical hacker.
Continuous learning and professional growth: The field of cybersecurity is ever-evolving, and learning CEH helps you stay updated with the latest threats, vulnerabilities, and countermeasures. It offers opportunities for continuous learning and professional development in the dynamic cybersecurity industry.
Make a positive impact: By learning ethical hacking, you can contribute to creating a more secure digital environment, protecting individuals and organizations from cyber threats, and making a positive impact on society.
Personal interest and curiosity: If you have a keen interest in technology, cybersecurity, and understanding how computer systems can be secured, learning CEH can be a fulfilling and rewarding experience.
Gain recognition and credibility: CEH certification is globally recognized and validates your knowledge and skills in ethical hacking. It enhances your professional credibility and demonstrates your commitment to ethical practices in cybersecurity.
The Certified Ethical Hacker (CEH) course is beneficial for individuals from various fields who want to enhance their Certified Ethical Hacker (CEH) abilities. This course is ideal for:
The pre-requisites for the Certified Ethical Hacker (CEH) course may include the following:
Basic IT knowledge: A foundational understanding of computer networks, operating systems, and general IT concepts is beneficial for grasping the CEH course material.
Familiarity with networking: Having knowledge of TCP/IP protocols, network architecture, and network security fundamentals is helpful in understanding the concepts covered in the CEH course.
Security fundamentals: Prior knowledge of cybersecurity principles, such as access controls, encryption, firewalls, and vulnerability assessments, provides a good foundation for the CEH course.
Experience with operating systems: Familiarity with popular operating systems like Windows and Linux is recommended, as the CEH course involves practical exercises and hands-on labs that may require interacting with these systems.
Ethical mindset: It is essential to have an ethical mindset and a strong understanding of the legal and ethical implications surrounding the use of hacking techniques. The CEH course focuses on ethical hacking practices, and students should adhere to professional and legal standards.
Learning commitment: The CEH course requires dedication and commitment to complete the training and prepare for the certification exam. Being motivated and willing to invest time and effort in learning the course material is crucial for success.
In addition to the mentioned courses, Sambodhi and Education Nest offer a range of other niche courses to cater to diverse learning needs. Some of the notable courses include:
Cassandra: Learn Cassandra, a highly scalable and distributed NoSQL database, to handle large amounts of data across multiple servers while ensuring high availability and fault tolerance.
Informatica: Gain expertise in Informatica, a leading data integration and management tool, to extract, transform, and load data from various sources, enabling efficient data integration and analysis.
Teradata: Master Teradata, a powerful analytics platform used by major organizations, to store, process, and analyze large volumes of data, enabling data-driven decision-making and business insights.
OpenShift: Explore OpenShift, a containerization platform developed by Red Hat, to build, deploy, and manage applications in a containerized environment, providing scalability and flexibility.
MongoDB: Discover MongoDB, a popular NoSQL database, and learn how to store, retrieve, and manage data in a flexible and scalable manner, empowering efficient data handling.
DevOps: Acquire skills in DevOps, a software development approach combining development and operations, to enhance collaboration, automate processes, and accelerate software delivery.
Data Science: Dive into the world of Data Science and learn techniques to extract insights from data, apply statistical analysis, and build predictive models to drive informed decision-making.
Salesforce: Develop expertise in Salesforce, a leading customer relationship management (CRM) platform, to manage customer data, automate sales processes, and optimize customer engagement.
WebLogic: Gain knowledge of WebLogic, an application server platform, to deploy, manage, and scale Java applications, ensuring efficient performance and high availability.
Agile using Scrum: Understand Agile principles and the Scrum framework, enhancing project management skills for efficient and adaptive project delivery.
These courses provide professionals with the opportunity to expand their skill set and stay relevant in the ever-evolving IT industry.
The Certified Ethical Hacker (CEH) course provides comprehensive training in ethical hacking techniques and methodologies. It equips individuals with the skills and knowledge to identify and exploit vulnerabilities in computer systems and networks, with the ultimate goal of enhancing overall security. Participants learn about various hacking tools, attack vectors, and countermeasures to protect organizations from malicious cyber threats. The course covers topics such as network scanning, system hacking, social engineering, cryptography, and web application security. Through a combination of theoretical knowledge and practical hands-on exercises, aspiring professionals gain the necessary expertise to become ethical hackers and contribute to the robustness of cybersecurity frameworks.
The objectives of the Certified Ethical Hacker (CEH) course are as follows:
There are several reasons why learning the Certified Ethical Hacker (CEH) course can be beneficial. Here are the key points:
Enhance cybersecurity skills: The CEH course equips you with in-depth knowledge and practical skills to identify vulnerabilities and strengthen the security of computer systems and networks.
Stay ahead of cyber threats: As the frequency and sophistication of cyberattacks continue to rise, organizations need professionals who can proactively identify and mitigate potential risks. CEH certification demonstrates your expertise in ethical hacking and makes you valuable in the job market.
Career opportunities: The demand for cybersecurity professionals, including ethical hackers, is growing rapidly. By gaining CEH certification, you open doors to a wide range of job opportunities in industries such as IT, finance, healthcare, government, and more.
Protect organizations from malicious hackers: With CEH skills, you can help organizations protect their sensitive data, prevent security breaches, and minimize the potential damage caused by cybercriminals.
Gain an understanding of hacker techniques: Learning ethical hacking provides insights into the mindset and techniques used by malicious hackers. This knowledge can be valuable in developing effective security measures and strategies.
Ethical hacking as a profession: Ethical hackers are hired by organizations to conduct security assessments, vulnerability testing, and penetration testing. The CEH course equips you with the necessary skills to pursue a career as an ethical hacker.
Continuous learning and professional growth: The field of cybersecurity is ever-evolving, and learning CEH helps you stay updated with the latest threats, vulnerabilities, and countermeasures. It offers opportunities for continuous learning and professional development in the dynamic cybersecurity industry.
Make a positive impact: By learning ethical hacking, you can contribute to creating a more secure digital environment, protecting individuals and organizations from cyber threats, and making a positive impact on society.
Personal interest and curiosity: If you have a keen interest in technology, cybersecurity, and understanding how computer systems can be secured, learning CEH can be a fulfilling and rewarding experience.
Gain recognition and credibility: CEH certification is globally recognized and validates your knowledge and skills in ethical hacking. It enhances your professional credibility and demonstrates your commitment to ethical practices in cybersecurity.
The Certified Ethical Hacker (CEH) course is beneficial for individuals from various fields who want to enhance their Certified Ethical Hacker (CEH) abilities. This course is ideal for:
The pre-requisites for the Certified Ethical Hacker (CEH) course may include the following:
Basic IT knowledge: A foundational understanding of computer networks, operating systems, and general IT concepts is beneficial for grasping the CEH course material.
Familiarity with networking: Having knowledge of TCP/IP protocols, network architecture, and network security fundamentals is helpful in understanding the concepts covered in the CEH course.
Security fundamentals: Prior knowledge of cybersecurity principles, such as access controls, encryption, firewalls, and vulnerability assessments, provides a good foundation for the CEH course.
Experience with operating systems: Familiarity with popular operating systems like Windows and Linux is recommended, as the CEH course involves practical exercises and hands-on labs that may require interacting with these systems.
Ethical mindset: It is essential to have an ethical mindset and a strong understanding of the legal and ethical implications surrounding the use of hacking techniques. The CEH course focuses on ethical hacking practices, and students should adhere to professional and legal standards.
Learning commitment: The CEH course requires dedication and commitment to complete the training and prepare for the certification exam. Being motivated and willing to invest time and effort in learning the course material is crucial for success.
In addition to the mentioned courses, Sambodhi and Education Nest offer a range of other niche courses to cater to diverse learning needs. Some of the notable courses include:
Cassandra: Learn Cassandra, a highly scalable and distributed NoSQL database, to handle large amounts of data across multiple servers while ensuring high availability and fault tolerance.
Informatica: Gain expertise in Informatica, a leading data integration and management tool, to extract, transform, and load data from various sources, enabling efficient data integration and analysis.
Teradata: Master Teradata, a powerful analytics platform used by major organizations, to store, process, and analyze large volumes of data, enabling data-driven decision-making and business insights.
OpenShift: Explore OpenShift, a containerization platform developed by Red Hat, to build, deploy, and manage applications in a containerized environment, providing scalability and flexibility.
MongoDB: Discover MongoDB, a popular NoSQL database, and learn how to store, retrieve, and manage data in a flexible and scalable manner, empowering efficient data handling.
DevOps: Acquire skills in DevOps, a software development approach combining development and operations, to enhance collaboration, automate processes, and accelerate software delivery.
Data Science: Dive into the world of Data Science and learn techniques to extract insights from data, apply statistical analysis, and build predictive models to drive informed decision-making.
Salesforce: Develop expertise in Salesforce, a leading customer relationship management (CRM) platform, to manage customer data, automate sales processes, and optimize customer engagement.
WebLogic: Gain knowledge of WebLogic, an application server platform, to deploy, manage, and scale Java applications, ensuring efficient performance and high availability.
Agile using Scrum: Understand Agile principles and the Scrum framework, enhancing project management skills for efficient and adaptive project delivery.
These courses provide professionals with the opportunity to expand their skill set and stay relevant in the ever-evolving IT industry.
Certified Ethical Hacker (CEH) Certificate Training Course reviews
Read learner testimonials
Mohit S.
Excellent faculty and a great learning experience. The courses are well worth the money spent, and the support is excellent if you have questions about the lectures or anything else. If you have a registration on the Sambodi and Education Nest platforms, you have the option to select your own batch based on your preferences.
Ayush G.
Sambodhi and Education Nest is the best e-learning platform. I will definitely suggest my friends join Sambodhi. The instructor and management are outstanding. The knowledge that the trainer shares with the student are excellent, and the sessions are very interactive. I will definitely join Sambodhi and Education Nest for other courses.
Asen S.
This Certified Ethical Hacker (CEH) course is so appropriate to my needs, that i enjoyed doing it and learnt so many valuable concepts/options that will surely help me in being a Certified Ethical Hacker. Thank you once again for a remarkable learning experience.
Hear from our learners
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Like what you hear from our learners?
Creating Epic Presentations: Communicating Powerful Ideas reviews
Certified Ethical Hacker (CEH) Training FAQs
If you miss an online Certified Ethical Hacker (CEH) Training class, it’s important to reach out to the instructor or the support team of the online training platform you are using. They may be able to provide you with a recording or transcript of the missed class, so that you can catch up on what you missed. Alternatively, some platforms offer on-demand access to class materials, so you can go back and review the content on your own time. It’s always a good idea to try and make up the missed material as soon as possible, so that you don’t fall behind in your learning.
If you have queries after completing an online Certified Ethical Hacker (CEH) Training course, Education Nest training platforms offer some form of post-course support. This may include access to a dedicated support team, a community forum where you can ask questions and connect with other learners, or even one-on-one sessions with an instructor or coach. If you have specific questions or concerns related to the course material, you can reach out to the instructor directly or use the support channels provided by the platform. It’s always a good idea to clarify any doubts or questions you may have, as this will help to solidify your understanding of the material and ensure that you can apply what you’ve learned in a real-world context.
Certified Ethical Hacker (CEH) is a professional certification that validates the skills and knowledge of individuals in the field of ethical hacking. Ethical hackers, also known as white hat hackers, use their expertise to identify vulnerabilities and weaknesses in computer systems and networks with the permission of the owners. The CEH certification program equips individuals with the necessary tools and techniques to assess security measures, detect potential threats, and propose countermeasures to protect systems from malicious activities. It covers various topics such as network scanning, system hacking, web application security, cryptography, and more. The CEH certification is widely recognized and sought after by organizations to ensure the security of their networks and systems.
The timing of when you get access to learning content after signing up for an online Certified Ethical Hacker (CEH) Training course will depend on the specific training platform you are using. In most cases, you should receive access to the learning content immediately upon signing up, or shortly after your payment has been processed. Some platforms may require you to complete an enrolment process or set up an account before you can access the content. It’s always a good idea to check the specific details of the course or platform you are using, as the timing and process may vary. If you are experiencing any issues accessing the learning content, you should contact the support team of the training platform for assistance.
Once you enrol in Certified Ethical Hacker (CEH) Training course, you will typically have access to the course material for as long as the course remains available on the platform. This means that you can revisit the material at any time, even after you have completed the course, and continue to learn and improve your skills. The benefit of lifetime access to the learning material is that it allows you to learn at your own pace and on your own schedule. You can review the content as many times as you need to fully understand the concepts and techniques covered in the course. Additionally, if you encounter a new challenge in your work or personal life, you can go back to the course material to find solutions and strategies to help you overcome the challenge. Having access to course material for a lifetime is a valuable benefit, as it allows you to continue to improve your skills and knowledge long after you have completed the course. So, if you are interested in improving your Communication skill, build confidence and want the flexibility to learn at your own pace, consider enrolling in Certified Ethical Hacker (CEH) Training course that offers lifetime access to the learning material.
If you miss an online Certified Ethical Hacker (CEH) Training class, it’s important to reach out to the instructor or the support team of the online training platform you are using. They may be able to provide you with a recording or transcript of the missed class, so that you can catch up on what you missed. Alternatively, some platforms offer on-demand access to class materials, so you can go back and review the content on your own time. It’s always a good idea to try and make up the missed material as soon as possible, so that you don’t fall behind in your learning.
If you have queries after completing an online Certified Ethical Hacker (CEH) Training course, Education Nest training platforms offer some form of post-course support. This may include access to a dedicated support team, a community forum where you can ask questions and connect with other learners, or even one-on-one sessions with an instructor or coach. If you have specific questions or concerns related to the course material, you can reach out to the instructor directly or use the support channels provided by the platform. It’s always a good idea to clarify any doubts or questions you may have, as this will help to solidify your understanding of the material and ensure that you can apply what you’ve learned in a real-world context.
Certified Ethical Hacker (CEH) is a professional certification that validates the skills and knowledge of individuals in the field of ethical hacking. Ethical hackers, also known as white hat hackers, use their expertise to identify vulnerabilities and weaknesses in computer systems and networks with the permission of the owners. The CEH certification program equips individuals with the necessary tools and techniques to assess security measures, detect potential threats, and propose countermeasures to protect systems from malicious activities. It covers various topics such as network scanning, system hacking, web application security, cryptography, and more. The CEH certification is widely recognized and sought after by organizations to ensure the security of their networks and systems.
The timing of when you get access to learning content after signing up for an online Certified Ethical Hacker (CEH) Training course will depend on the specific training platform you are using. In most cases, you should receive access to the learning content immediately upon signing up, or shortly after your payment has been processed. Some platforms may require you to complete an enrolment process or set up an account before you can access the content. It’s always a good idea to check the specific details of the course or platform you are using, as the timing and process may vary. If you are experiencing any issues accessing the learning content, you should contact the support team of the training platform for assistance.
Once you enrol in Certified Ethical Hacker (CEH) Training course, you will typically have access to the course material for as long as the course remains available on the platform. This means that you can revisit the material at any time, even after you have completed the course, and continue to learn and improve your skills. The benefit of lifetime access to the learning material is that it allows you to learn at your own pace and on your own schedule. You can review the content as many times as you need to fully understand the concepts and techniques covered in the course. Additionally, if you encounter a new challenge in your work or personal life, you can go back to the course material to find solutions and strategies to help you overcome the challenge. Having access to course material for a lifetime is a valuable benefit, as it allows you to continue to improve your skills and knowledge long after you have completed the course. So, if you are interested in improving your Communication skill, build confidence and want the flexibility to learn at your own pace, consider enrolling in Certified Ethical Hacker (CEH) Training course that offers lifetime access to the learning material.
Be future ready, start learning